Unified Endpoint Manager
Creation
Portal
Support
Solutions
Service
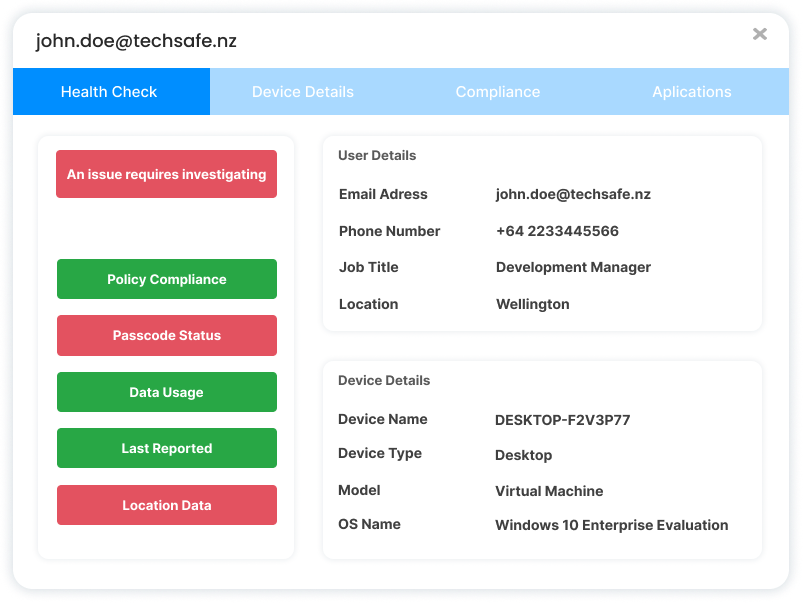
At TechSafe we are about making Unified Endpoint Management (MDM) simple, improving customers security, reducing costs, and providing rich asset visibility. We offer a full worry-free managed service that includes license management, Threat protection, and advanced AI-enabled analytics.