TechSafe Comply offers a flexible suite of services designed to provide your organization with a streamlined and effective path to achieving compliance with leading security and privacy frameworks. Our approach is powered by Vanta, a leading and trusted compliance management platform that supports over 35 global standards and regulations, including ISO/IEC 27001, NIST, GDPR, and SOC 2.
We work collaboratively to tailor a compliance strategy aligned with your organization’s specific requirements, timelines, and resource availability—defined during an initial discovery phase. This strategy is delivered transparently and tracked in real time using Vanta’s compliance dashboard, giving your leadership team full visibility into progress and milestones throughout this critical phase of your compliance journey.




Market Advantage, Trust & Reputation
Demonstrating compliance builds trust with customers, partners, and investors. It signals a commitment to data protection and operational integrity, which can be a key differentiator in competitive markets—especially in sectors like government, finance, healthcare, and SaaS.
Risk Mitigation & Incident Prevention
Compliance with recognized frameworks (e.g., ISO/IEC 27001, NIST, SOC 2) helps identify and address vulnerabilities before they can be exploited. This proactive approach significantly reduces the likelihood of data breaches, ransomware attacks, and operational disruptions—protecting both reputation and revenue.
Regulatory & Contractual Assurance
Meeting compliance standards ensures alignment with legal and industry-specific standards and regulations such as ISO 27001, GDPR, HIPAA, or PCI-DSS. It also strengthens your position in contractual negotiations, especially with enterprise clients who require demonstrable security controls and audit readiness.
Capella Consulting provides a range of TechSafe Comply Services to assist organisations of any size and nature to achieve their compliance requirements. Each can be tailored to your particular requirements.
| Service | Description |
| Comply Subscription | Access to the Vanta solution with one or more compliance frameworks. This includes a Vanta introduction session to get your compliance team familiar with the product. |
| Comply Fast Start | A tailored consulting session to get the basic configurations in place, such as company setup, staff imports, service integrations, and Statement of Applicability – selecting the controls and tests that are applicable to your organisation and requirements. Depending on the size and complexity of your organisation this will typically take between two and five working days |
| Comply Assist | A tailored consulting service to assist your compliance team to achieve internal audit readiness. Depending on the size and complexity of your organisation this will typically involve one or two days per week. |
| Comply Journey | A tailored consulting service to drive your compliance efforts managing Vanta and your compliance team to achieve internal audit readiness. Depending on the size and complexity of your organisation and your compliance requirements, this will typically take between two and five working days per week. |
| Internal Audit | The final stage prior to the external audit and certification. The internal audit will establish whether the external audit will be passed with confidence. Depending on the size and complexity of your organisation this will typically take between three and five working days |
| External Auditor Recommendation | We can recommend external auditors who are familiar with Vanta or alternatively you can commission an auditor of your choice. |
ISO 27001 Compliance is effectively a 3-year cycle following the certification.
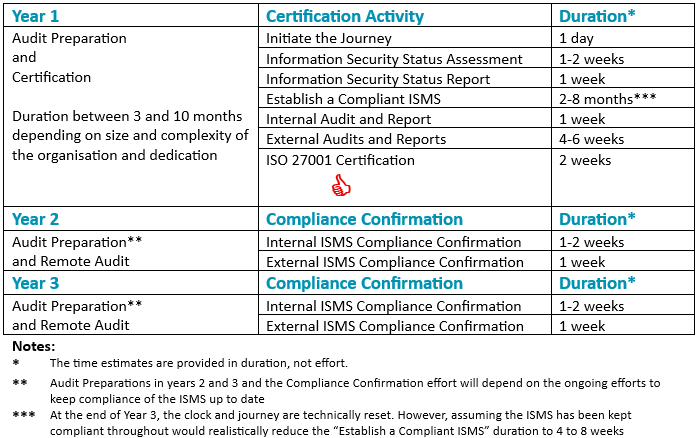
Initiate the Journey – 1 day
Opening meeting with senior management and security team to describe the route demonstrate the Vanta toolset and set expectations for the following stage.
Information Security Status Assessment – 1-2 weeks
Assessment of your current ISMS related measures and status.
Information Security Status Report – 1 week
A summary report of current status and high-level plan to achieve compliance.
Establish a Compliant ISMS – 2-8 months
We guide and assist your organisation to establish or remediate your ISMS to be ISO 27001 compliant.
Internal Audit and Report – 1 week
One of our independent auditors assess your certification readiness.
External Audits and Reports – 4-6 weeks
Two external certified and independent auditors assess your compliance in a two-phase audit.
ISO 27001 Certification – 2 weeks
At the close of the second phase external audit compliance is confirmed but formal certification can take up to 10 days.
Year One and Year Two Audits and Reports
12 and 24 months after certification two external audits are conducted to confirm ongoing compliance.
If your organisation is prioritising Cyber Threat Preparedness or Information Security Compliance, we can advise, guide and assist – tailored to your needs
We are ready to make any of those stages transparent and manageable
Feel free to connect with our experts—they are here to guide you toward the most suitable solution for your organization and assist you with your implementation.
We empower organizations with innovative expertise in IT governance, IT fleet management, risk management, and compliance—delivering strategic solutions across cyber resilience, data protection, cybersecurity, and business continuity.

ISO 27001 is a globally recognized standard for managing information security. It offers a structured framework for developing, operating, maintaining, and continuously enhancing an organization’s Information Security Management System (ISMS). The standard emphasizes safeguarding the confidentiality, integrity, and availability of information by promoting a risk-based approach to identifying and addressing security threats. It also guides the implementation of appropriate controls and the establishment of processes for regular monitoring and improvement. Achieving ISO 27001 compliance reflects an organization’s dedication to information security best practices.

A Security Operations Centre (SOC) is a centralized team or facility tasked with continuously monitoring and analysing an organization’s cybersecurity landscape. Its primary role is to detect, investigate, and respond to security threats using a range of tools and technologies. By examining network traffic, log data, and security systems, the SOC works to identify and mitigate potential cyber-attacks, ensuring the ongoing protection and integrity of the organization’s information systems.
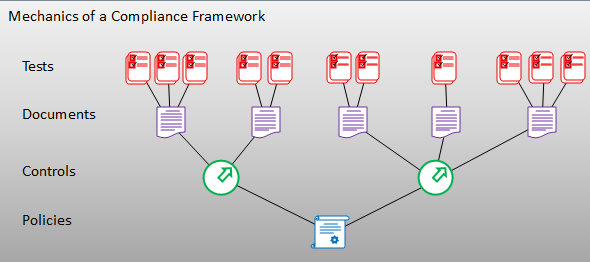
Although various frameworks may differ in terminology or place emphasis on slightly different aspects, they typically align with the underlying model outlined below. For this example, ISO 27001 will serve as our reference framework.
The standard developed by the International Standards Organisation divides a business into its fundamental activities, each defined by a hierarchy of processes and sub-processes. Ultimately, the framework establishes a set of controls designed to protect and steer these processes.
A business must establish policies that operate within the boundaries defined by those controls. Supporting systems should generate evidence to demonstrate compliance, typically in the form of one or more documents or other forms of measurable evidence, like the unresolved vulnerabilities of a given system.
To ensure ongoing compliance, validation mechanisms should be implemented to verify that the evidence aligns with policy requirements and, by extension, supports the underlying controls.
Vanta will automate cross-referencing policies, controls, documents, and tests. It will track currency of the materials and automate controls around approvals and staff acceptance of certain materials.
While both aim to strengthen an organization’s security posture, and ISO 27001 and a Security Operations Centre (SOC) differ in the various facets, touched on below.
Scope
ISO 27001 takes a broad, organization-wide view. It integrates information security principles across people, processes, and technologies, ensuring a unified and systematic approach to managing security risks.
The SOC scope is narrower and functions as an operational unit staffed with analysts and equipped with tools to monitor and address security threats as they arise.
Focus
ISO 27001 is a strategic framework for building and maintaining an Information Security Management System (ISMS). It emphasizes risk assessment, policy creation, control implementation, and continuous improvement.
A SOC, by contrast, is centred on the real-time detection, analysis, and response to security incidents. This includes activities like threat monitoring, incident response, and security event analysis.
Objectives
ISO 27001 aims to develop a robust Information Security Management System (ISMS) that protects the confidentiality, integrity, and availability of information. It also ensures compliance with applicable legal, regulatory, and contractual obligations.
On the other hand, the core goal of a Security Operations Centre (SOC) is to swiftly detect, analyze, and respond to security incidents in order to limit the damage of breaches and safeguard vital assets.
Compliance
ISO 27001 compliance demands a structured approach through the formal implementation of an Information Security Management System (ISMS), as outlined by the standard. This encompasses conducting risk assessments, creating, and enforcing policies, deploying controls, and undergoing periodic audits to validate alignment.
Conversely, SOC compliance does not adhere to a singular standard; instead, it gauges how effectively an organization follows established cybersecurity best practices. SOC operations are often aligned with broader industry frameworks or specific regulatory obligations.
ISO Certification and SOC Reports
ISO independent accreditation bodies authorize and monitor certification bodies to ensure they and their auditors operate according to international norms. JAS-ANZ is the joint Accreditation System of Australia and New Zealand. Auditors of the certification body measure compliance of your implemented ISMS against the standard. SOC uses accredited accountants who measure your incident and response readiness and present a report on their findings. There are three different SOC reports:
SOC-1 and SOC-2 reports can also be produced in Type-1 and Type-2:
In Summary
Facet | ISO 27001 | SOC |
Scope | Implementation spanning the entire organization | Dedicated organisational function |
Focus | Information Security Management | Active security incident response |
Compliance | Compliance with the ISO standard | Adherence to frameworks, best practice often encouraged by regulations or legislations |
Objectives | Risk management, compliance with a fit for purpose ISMS | Incident discovery, investigation, and response |
Actions | Policy definition, deployment of controls surrounded by risk assessment | Threat awareness and pursuit, incident response, post security event investigation |
Association | A comprehensive ISMS framework | Can technically be part of another framework |
Market | Global orientation | United States oriented |
Certification | ISO 27001-accredited certification body | Licensed CPA (Certified Public Accountant) |
Certificate | Certificate of compliance | Formal attestation |
Period | Three years with intermediate audits at the beginning of years two and three | One year |

The above discussion would be incomplete without a mention of GDPR.
GDPR takes a somewhat alternative approach towards information security.
The essence of the General Data Protection Regulation (GDPR) lies in its mission to protect the personal data and privacy of individuals within the European Union (EU) and beyond.
GDPR is designed to:
The Seven Key Principles of GDPR
These principles guide how personal data should be held and processed:
Rights for Individuals
GDPR empowers individuals with rights such as:
Global Impact
Even non-EU organizations must comply if they handle data of EU residents. Non-compliance can lead to significant fines and reputational damage
Certification Validity
GDPR certification has a maximum validity of three years.
There are intermediate audits, but they are determined by the certification scheme as it applies to your business and the risk profile of your business.
Ideally, the information above has helped clarify whether ISO 27001 or SOC 2 is a better fit for your organization. While SOC 2 tends to be more cost-effective and simpler to implement, it is generally considered less comprehensive and less rigorous than ISO 27001.
While ISO 27001 requires greater effort to implement and maintain, it offers a more robust framework for safeguarding organizations against information security threats.
The Global Impact statement of GDPR determine whether that standard and its compliance is most suitable. If your organisation handles data of EU citizens, you are legally responsible to be GDPR compliant.
Feel free to connect with our experts—they are here to guide you toward the most suitable solution for your organization and assist you with your implementation.
We empower organizations with innovative expertise in IT governance, IT fleet management, risk management, and compliance—delivering strategic solutions across cyber resilience, data protection, cybersecurity, and business continuity.
International Standardisation Organisation – ISO
Global standards are for trusted goods and services.
Standards define what great looks like.
Setting consistent benchmarks for businesses and consumers alike — ensuring reliability, building trust, and simplifying choices.
Making lives easier, safer, and better.
What can standards do for you?
International standards help ensure that the products and services you provide or rely on are safe, dependable, and high-quality. They also encourage businesses to embrace sustainable and ethical practices, shaping a future where your purchases not only deliver exceptional performance but also mindful of their environmental impact. Ultimately, standards integrate excellence with responsibility, enriching both daily life and consumer choices.
What is ISO/IEC 27001?
ISO/IEC 27001 is the most widely recognized standard for information security management systems (ISMS). It outlines the essential requirements that an ISMS must fulfil to ensure robust security practices.
ISO/IEC 27001 offers organizations of all sizes and industries a comprehensive framework for developing, implementing, maintaining, and continuously enhancing their information security management system (ISMS). It ensures a structured approach to safeguarding sensitive data and managing security risks effectively.
Conformity with ISO/IEC 27001 signifies that an organization has implemented a structured system to manage risks associated with the security of its data. It ensures that the company follows industry best practices and principles outlined in this internationally recognized standard.
Why is ISO/IEC 27001 important?
As cyber threats continue to evolve, managing risks can feel overwhelming. ISO/IEC 27001 equips organizations with the tools to stay ahead by fostering risk awareness and enabling proactive identification and mitigation of vulnerabilities.
ISO/IEC 27001 takes a comprehensive approach to information security, evaluating people, policies, and technology. An ISMS designed in line with this standard serves as a powerful tool for managing risks, strengthening cyber resilience, and driving operational excellence.
Compliance Escalation
Compliance escalation has evolved significantly over the past two or three decades, driven by increasing regulatory complexity, technological advancements, and heightened corporate accountability. Organizations have implemented more structured mechanisms for reporting and addressing compliance concerns, with many adopting formal escalation procedures to ensure transparency and mitigate risks.
Compliance Priority
Recent surveys indicate that companies are prioritizing compliance innovation, leveraging digital transformation to navigate regulatory challenges more efficiently. Additionally, emerging risks—such as fraud and cybersecurity threats—have intensified the need for proactive compliance measures.
Future Certainty
Most, if not all of the countries we benchmark ourselves against have, for distinct reasons, advanced further in their compliance frameworks and regulatory journeys. In jurisdictions such as Australia and across the European Union, regulatory compliance has become a fundamental prerequisite for conducting business. There is certainty that our future in New Zealand will follow in that trajectory.
The Compliance Journey
Achieving compliance, the duration, the impact, and the effort are dependent on a wide range of aspects but starts and ends with commitment.
The maturity of the organisation, its size and the complexity of its business model all have further influence on the journey.
The latter three can all be managed and/or reduced through the use of a tool that is fit for purpose.
Vanta
In essence, automation of compliance aspects that simplify tasks and efforts are Vanta’s forté. Through out-of-the-box integrations, Vanta will import required objects or their status and cross-check them against requirements and applicability. The system integrates with many hundreds of systems ranging from background checkers to vulnerability scanners. Those integrations link critical information related to the ISMS to provide a holistic view and compliance status across the organisation. Using Vanta in a multi-tiered standards scenario is extremely expedient. It removes duplication and provides holistic compliance overview.
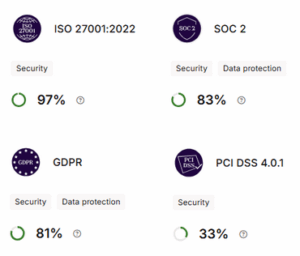
The above shows that our current ISO 27001 compliance measure of 97% puts us at the indicated levels of SOC, GDPR, and PCI DSS compliance.
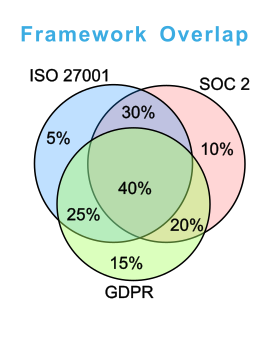
Above percentages are indicative only. Compliance overlap will vary per business depending on elected controls as they apply to a particular business.
Compliance for many organisations is driven by their commitment to keeping data and systems secure and employing that posture in marketing and sales efforts. Trust Centre can be published to your customers where they can view your compliance status and efforts and also gain or request access to your compliance artefacts.
Automate Compliance. Simplify Security. Demonstrate Trust
Vanta is the leading trust management platform that helps simplify and centralize security for organizations of all sizes.
Thousands of companies rely on Vanta to build, maintain and demonstrate their trust—all in a way that’s real-time and transparent.
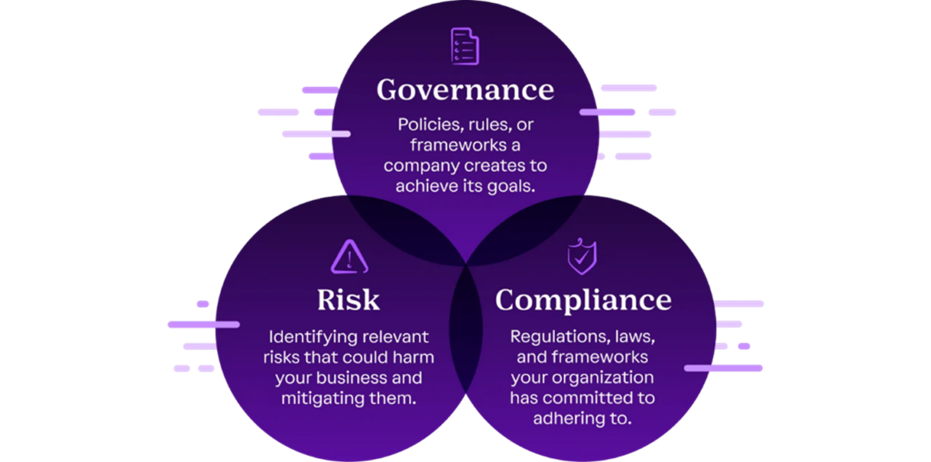
Governance, Risk and Compliance (GRC) is a well-established and structured approach to align ICT with business objectives.
Vanta centralises the collection and management of GRC artefacts and supports processes to keep those artifacts up to date and relevant.
To achieve compliance, Vanta provides a wide range of templates and in-depth guidance to expedite the preparation activities and processes.
During the initial setup stage of Vanta it will be connected to relevant systems and service providers you may have to broaden its integration base.
By virtue of the system having contextual knowledge of compliance artefacts, their controls and systems knowledge related to those artefacts, Vanta will automate certain elements and activities of the compliance journey.
Governance, Risk and Compliance (GRC) program requires more time and resources to manage than ever before. With increasing security expectations from customers, growing requirements to scale compliance across additional frameworks, and the need to track a growing list of vendors, the burden of your GRC program is ever-increasing. As the workload steepens, you have fewer hours to focus on strategic work that strengthens the security posture of your organization and drives innovation within the security function. Your GRC program needs tools that enable continuous compliance—to take work off your plate and help you manage and monitor changes across your controls and vendors—so you can focus on innovation.
Vanta provides a compliance platform designed to help businesses automate and streamline their compliance preparations and maintenance. Vanta aims to enhance trust in internet businesses by enabling companies to establish, achieve and prove compliance.
The rapid escalation of cyber threats has shifted the focus of compliance further towards the cyber protection components of compliance.
Vanta automates, simplifies and streamlines your compliance efforts by virtue of the following services it provides:
Vanta‘s mission is to secure the internet, increase trust in software companies, and keep consumer data safe. It helps businesses demonstrate their security posture to customers and potential buyers, thereby unlocking business growth and expansion into new markets.
The Vanta Trust Center is a customizable platform that enables organizations to publicly share their security and compliance posture. It centralizes key documents like audit reports, certifications, and policies, helping reduce repetitive security questionnaires and build trust with stakeholders.
Professionally, it streamlines security reviews and shortens sales cycles by allowing prospects to self-serve verified information. It integrates with tools like Salesforce and supports NDA workflows, access controls, and real-time updates, making it a valuable asset for security, sales, and compliance teams.
Vanta offers a structured rollout plan and ongoing optimization support, ensuring the Trust Center remains a reliable and up-to-date source of truth. It helps organizations demonstrate transparency and commitment to data protection, enhancing credibility and competitive advantage.
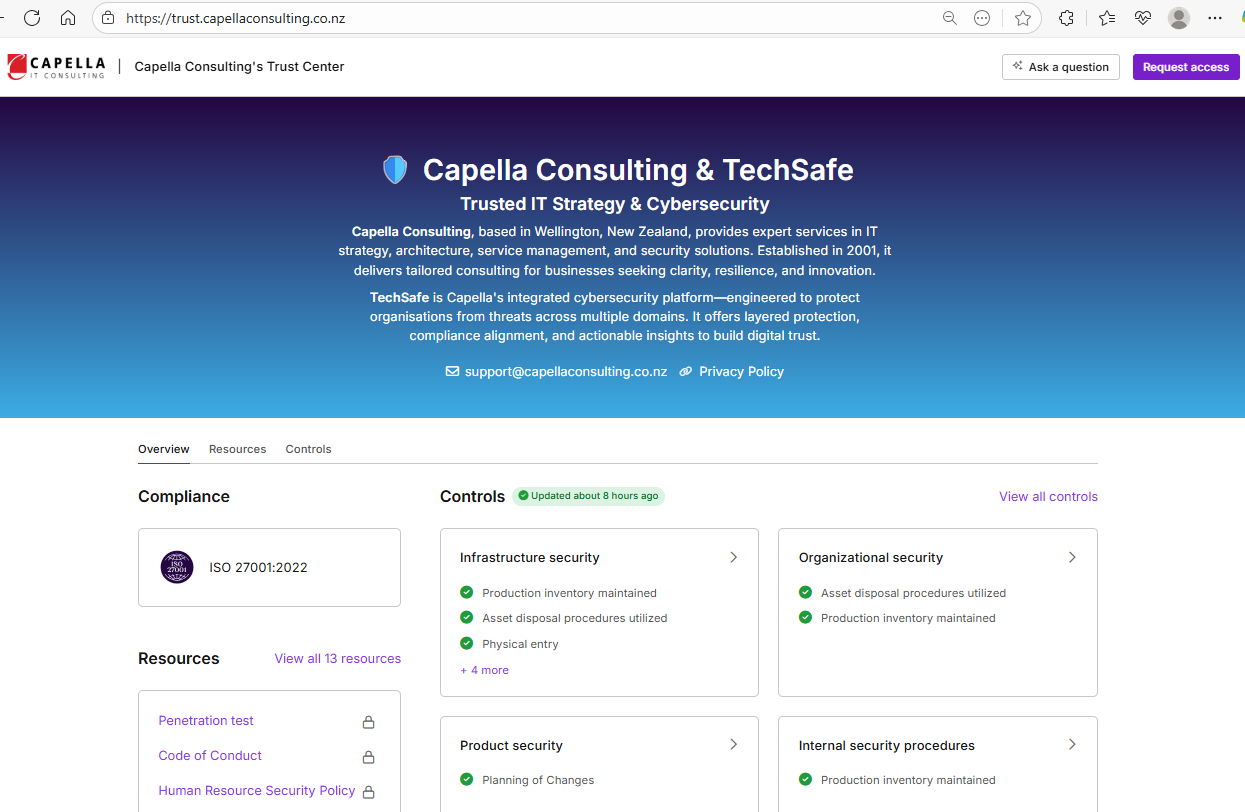
Capella Consulting’s security position can be viewed at Trust Center – Capella Consulting
Vanta supports the following compliance frameworks out of the box. Most are related to Information Security with exception of ISO 9001 and ISO 42001
Framework | Description |
23 NYCRR 500 | Title 23 NYCRR Part 500 is a regulation establishing cybersecurity requirements for financial services companies regulated by the NYDFS |
AI ACT | The EU AI Act is a regulation established by the European Parliament and the Council of the European Union to create a uniform legal framework for the development, placement on the market, and use of artificial intelligence (AI) systems within the Union. |
Australian Essential 8 | Commonly used and accepted requirements from the ACSC in Australia for hardening IT environments against attacks. Specifically designed to impose technical cost on attackers as opposed to be a broad information security and compliance governance framework. |
AWS FTR | AWS foundational technical review is a mandatory requirement for access to several AWS Partner benefits including, the AWS Competency Program and the AWS ISV Accelerate Program. |
CCPA | California regulation that gives residents new data privacy rights. For any for-profit company that does business with California residents. |
CIS v8.1 | The CIS Critical Security Controls (CIS Controls) are a prioritized set of Safeguards to mitigate the most prevalent cyber-attacks against systems and networks. They are mapped to and referenced by multiple legal, regulatory, and policy frameworks. |
CMMC 2.0 | The Cybersecurity Maturity Model Certification (CMMC) 2.0 program is the next iteration of the Department’s CMMC cybersecurity model. It streamlines requirements to three levels of cybersecurity and aligns the requirements at each level with well-known and widely accepted NIST cybersecurity standards. |
CPS 234 | The APRA Prudential Standard CPS 234 Information Security aims to ensure that an APRA-regulated entity takes measures to be resilient against information security incidents (including cyberattacks) by maintaining an information security capability commensurate with information security vulnerabilities and threats. |
DORA | The Digital Operational Resilience Act (DORA) aims to establish a comprehensive regulatory framework to ensure that all entities in the financial system have the necessary capabilities to withstand, respond to, and recover from ICT-related disruptions. |
FedRAMP r4 | FedRAMP is a security framework that cloud service providers and cloud-based products must meet in order to serve US Federal Agencies. |
FedRAMP r5 | FedRAMP r5 is a security framework that cloud service providers and cloud-based products must meet in order to serve US Federal Agencies. |
GDPR | European Union (EU) regulation to protect personal data and privacy of its citizens. For all companies that do business or have employees located in the EU. |
HIPAA | United States (US) regulation to secure Protected Health Information (PHI). For US companies that process, transmit, or store PHI data. |
HITRUST | The HITRUST Framework (HITRUST CSF®) is the comprehensive, scalable, reliable, and efficient framework for risk management and regulatory compliance. It’s designed to help organizations in any sector, big and small, local and global, adapt to new threats and new standards that may arise at any time. The framework is comprised of 3 assessment types e1, i1 and r2. |
ISO 27001:2022 | ISO 27001 is the international gold standard for information security management. Vanta ensures you conform to the latest version, ISO 27001:2022, to prove the strength of your security posture to prospects and customers in global markets |
ISO 27017 | ISO 27017 provides guidelines for information security controls applicable to the provision and use of cloud services. |
ISO 27018 | ISO 27018 establishes controls to protect Personally Identifiable Information (PII) in public cloud computing environments. |
ISO 27701 | ISO 27701 is a certifiable extension of ISO 27001 that specifies the requirements for establishing, implementing, maintaining and continually improving a privacy information management system (PIMS). |
ISO 42001 | ISO 42001 defines the requirements for establishing, implementing, maintaining and continually improving an AI management system for the responsible development, provision and use of AI systems. |
ISO 9001 | ISO 9001 is a globally recognized standard for quality management. It helps organizations of all sizes and sectors to improve their performance, meet customer expectations and demonstrate their commitment to quality. Its requirements define how to establish, implement, maintain, and continually improve a quality management system (QMS). |
MSFT SSPA | Microsoft SSPA is a mandatory compliance program for Microsoft suppliers working with Personal Data and/or Microsoft Confidential Data. |
MVSP | Minimum Viable Secure Product is a minimalistic security checklist for B2B software and business process outsourcing suppliers. |
NIS 2 | The NIS 2 Directive (Directive (EU) 2022/2555) establishes measures to achieve a high common level of cybersecurity across the European Union, aiming to improve the functioning of the internal market. The directive imposes cybersecurity risk-management measures and reporting obligations on certain public and private entities, promotes cybersecurity information sharing, and outlines supervisory and enforcement responsibilities for Member States |
NIST 800-171 | NIST 800-171 is a NIST Special Publication that provides recommended requirements for protecting the confidentiality of controlled unclassified information (CUI). It is a requirement for US defence contractors. |
NIST 800-53 | NIST 800-53 is a security framework that provides a catalogue of security and privacy controls for all U.S. federal information systems except those related to national security. |
NIST AI RMF | NIST AI RMF is a framework that provides guidance and structure for the identification, evaluation, and management of risks related to the use of AI systems. |
NIST CSF | NIST CSF is voluntary guidance, based on existing standards, guidelines, and practices for organizations to better manage and reduce cybersecurity risk. |
NIST CSF 2.0 | The NIST Cybersecurity Framework (CSF) 2.0 provides guidance to industry, government agencies, and other organizations to manage cybersecurity risks. It offers a taxonomy of high-level cybersecurity outcomes that can be used by any organization — regardless of its size, sector, or maturity — to better understand, assess, prioritize, and communicate its cybersecurity efforts. |
OFDSS | OFDSS is a modern, cloud first security framework that enhances data security for participants in the Open Finance system. |
PCI DSS | Industry-mandated requirements to secure cardholder data. SAQ D, SP and ROC prep support. For companies that process, transmit, or store cardholder data. |
PCI-DSS 4.0 | Industry-mandated requirements to secure cardholder data. Covers PCI-DSS ROC prep support for Merchants or Service Providers. Also supports SAQ-D Variants, SAQ A and SAQ-A EP by default. For companies that process, transmit, or store cardholder data or that impact the security of the processing, transmission or security of cardholder data. |
SOC 2 | SOC 2 (System and Organization Controls 2) is a compliance framework that evaluates an organization’s information security practices. It’s a must-have for building trust with stakeholders by demonstrating robust security measures. Ideal for SaaS companies and IT service providers, SOC 2 helps unlock business opportunities by assuring clients of your security posture. |
SOX ITGC | SOX ITGC is a set of IT controls required to be compliant with the Sarbanes-Oxley Act. |
TISAX | TISAX (Trusted Information Security Assessment Exchange) is a framework for assessing and exchanging information security standards among enterprises, allowing participants to recognize each other’s assessment results. It helps reduce efforts when processing sensitive customer information or evaluating the information security of your suppliers. |
UK Cyber Essentials | Commonly used and accepted requirements from the UK’s NCSC for hardening IT environments against attacks. Specifically designed to impose technical cost on attackers as opposed to be a broad information security and compliance governance framework. |
US Data Privacy | US Data Privacy ensures that companies comply with all applicable US Privacy Legislation including CCPA/CPRA (CA), UCPA (UT), CTDPA (CT), CPA (CO) and VCDPA (VA) law. |
Info@techsafe.nz
04 382 8096
Level 1
166 Featherston Street
Wellington Central
Wellington 6011
New Zealand
© 2025 techsafe.nz | All Rights Reserved